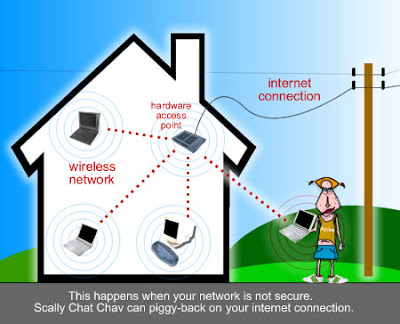
We all are facing the problem of Hacking in one or the other way. But do we all know about the laws in which that culprit "Cracker" can really be punished?
If not, then, HANS is making an effort to make you aware about your rights so that a right step can be taken at the right time so that this "CYBER TERRORISM" can actually be stopped.
Section 43 - Unauthorised Access means Using someone account without permission and authentication.
Under the IT Act, 2008 no limit on amount of compensation for offences under Section 43.
Under IT Act, 2008 all the acts referred under section 43, are also covered u/Sec. 66 if they are done "dishonestly" or "fraudulently".
Section 66(A) Sending of offensive or false messages , Also known as "Cyber Stalking"
Section 66(B) Dishonestly receiving stolen computer resource or communication device
Also covers use of stolen Computers, mobile phones, SIM Cards, etc
Punishment – imprisonment upto 3 years or fine upto Rs. 1 lakh or both
Section66(C) Identity theft
Fraudulently or dishonestly using someone else's electronic signature, password or any other unique identification feature.
Punishment - Imprisonment upto 3 years and fine upto Rs. 1 lakh
Section 66(D) Cheating by personation
Cheating by pretending to be some other person
Punishment – imprisonment upto 3 years and fine upto Rs. 1 lakh.
Covers sending of menacing, offensive or false messages via SMS/EMAIL/MMS
Punishment – imprisonment upto 3 years and fine.
Section 66(E) Violation of Privacy ,Popularly known as Voyeurism
Pune spy cam incident where a 58-year old man was arrested for installing spy cameras in his house to 'snoop' on his young lady tenants
Covers acts like hiding cameras in changing rooms, hotel rooms, etc
Punishment –Imprisonment upto 3 years or fine upto Rs. 2 lakh or both.
Section 66(F) Cyber terrorism
Whoever uses cyberspace with intent to threaten the unity, integrity, security or sovereignty of India or to strike terror in the people
Punishment - Imprisonment which may extent to life imprisonment
Section 67 - Publishing or transmitting obscene material in electronic form.
Punishment
First instance - imprisonment upto 3 years and fine upto Rs. 5 lakh.
Subsequent - imprisonment upto 5 years and fine upto Rs. 10 lakh.
Section 67(A) Cyber Pornography.
Publishing or transmitting sexually explicit acts in the electronic form
Similarity with Sec. 292 IPC
Punishment
First instance - imprisonment upto 5 years Subsequent - imprisonment upto 7 years Fine upto Rs. 10 lakh.
Section 67(B)
Creating, collecting, browsing, downloading, etc of Child Pornography
Punishment
First instance - imprisonment upto 5 years.
Subsequent - imprisonment upto 7 years
Fine upto Rs. 10 lakh.
Section 69 – Government's power to intercept
Government to intercept, monitor or decrypt any information generated through any computer resource if it thinks to do so in the interest of the sovereignty or integrity of India.
Section 67(C) – Preservation of information by intermediaries
Intermediary shall preserve and retain such information as may be specified for such duration and in such manner and format as the Central Government may prescribe.
Section 72(A) - Liability of Intermediary not to disclose any personal information
Intermediary to act as per the terms of its lawful contract and not beyond it.
Punishment – imprisonment upto 3 years or fine upto 5 lakh or both.
Section 79- Liability of Intermediary
An intermediary not to be liable for any third party information, data, or communication link made available or hosted by him.
Liability of Intermediary:-
Intermediary need to prove that he didn't –
* Initiate the transmission,
* Select the receiver of the transmission, and
* Select or modify the information contained in the transmission and
The intermediary observes due diligence while discharging his duties under the Act.
Section 84(B) – Abetment
Abetting to commit an offence is punishable
Punishment – Same punishment provided for the offence under the Act
Section 84(C) – Abetment
Attempt to commit an offence is punishable.
Punishment – Imprisonment which may extend to one-half of the longest term of imprisonment provided for that offence
Section 78 – Investigation Powers
As per the IT Act, 2008 Cyber crime cases can be investigated by the "Inspector" rank police officers.
Under the IT Act, 2000 such powers were with the "DYSP/ACP".
Section 77 (A) – Compounding of Offences
Compounding – "Out of court settlement"
Offences
* "for which less than three years imprisonment has been provided" can be compounded.
* Such offence should not affect the socio economic conditions of the country or
* has been committed against a child below the age of 18 years or a woman.
These are the"Laws" according to the "IT AMENDMENT ACT 2008" which was passed in 2009. We all should be aware of our CYBER RIGHTS, so that we together can fight with the "CYBER THREATS